Cybersecurity Lab
In the IoT generation, cybersecurity is a critical business risk that can cause unpredictable and huge losses. Anything connected to the internet has the potential to be hacked, especially smart/IoT devices are new targets for cyber threats.
Allion’s Cybersecurity Solutions will support you to effectively defend against cybercrimes, threats and attacks.

How to ensure your cybersecurity?
- Network and Perimeter Security
- Endpoint Security
- Application Security
- Data Security
- Identity and Access Management (IAM)
- Zero Trust Architecture.
How to Confirm Your Cybersecurity?
- Check OWASP Foundation outline critical security concerns periodically.
- Be quickly and flexible on your defense, critical concerns changed from time to time due to the growth of the cyber world.
- Consult to Allion, our cybersecurity solutions are refer to IoT discussions from OWASP and related association.
We will cover the most critical security risks and user scenarios.
You Could Be the Next Victim – Major Targets for Hackers
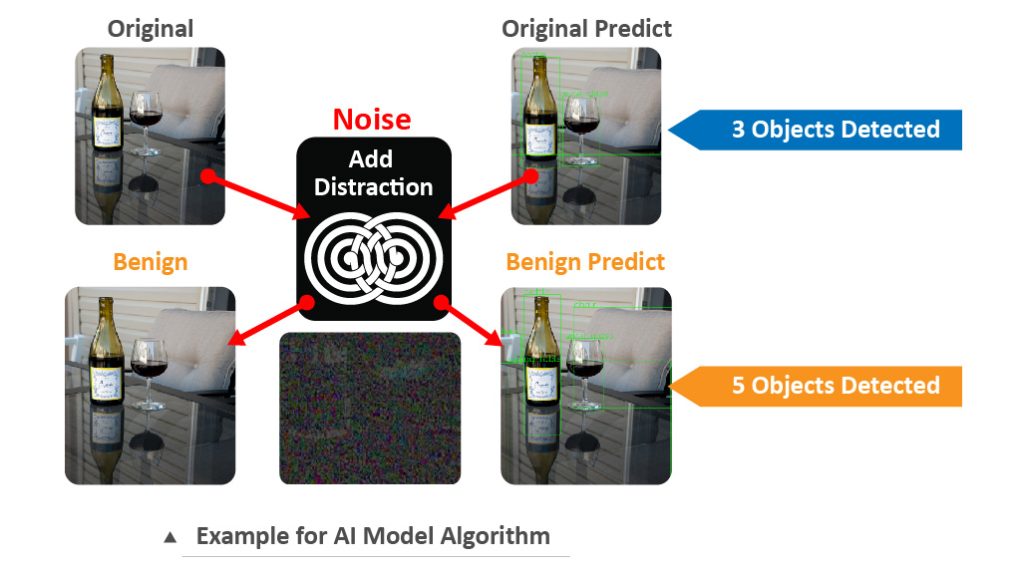
AI Model Algorithm

Allion + AI + Cybersecurity = Complete Protection
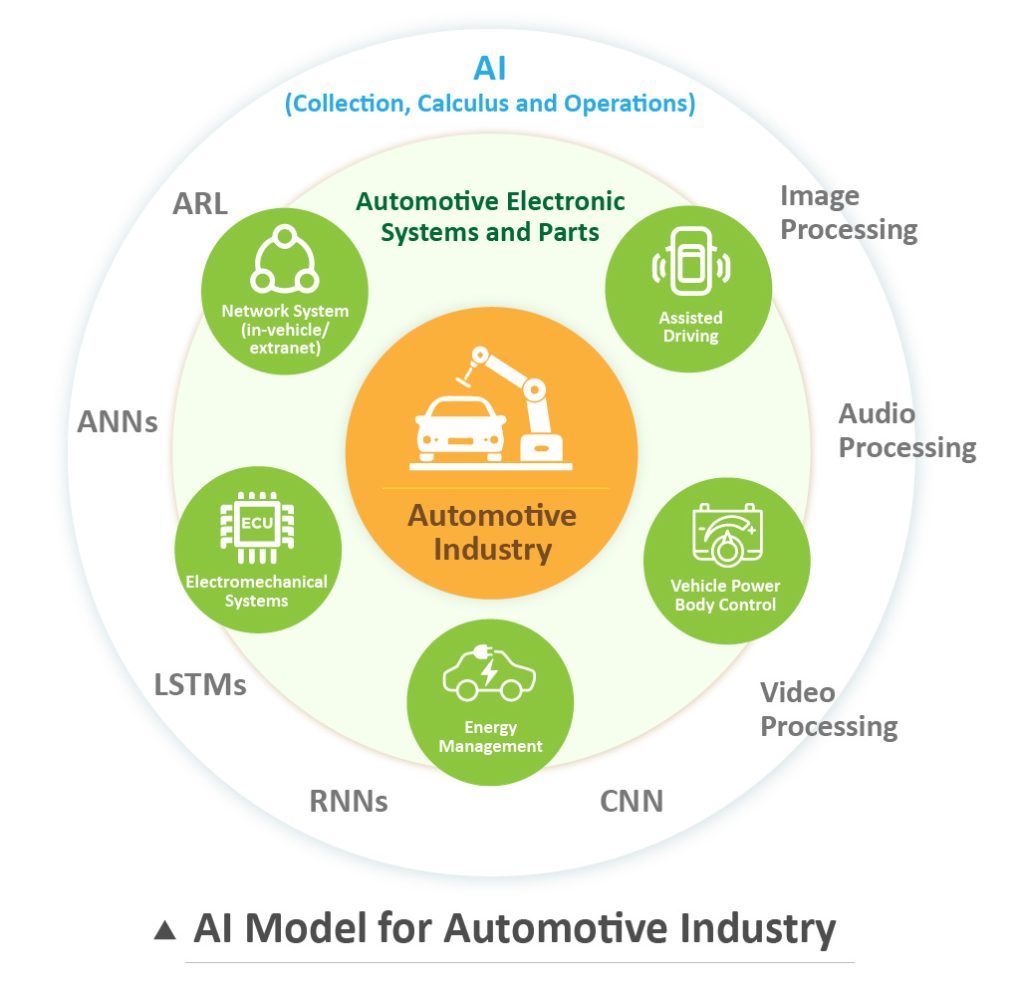
Allion use AI algorithms to perform test processes, with over 100 AI algorithms available for testing and modeling in a variety of industries. For example, most of the new products and innovative technologies are related to electronics, software, and IT in the automotive industry. The functional safety and cybersecurity requirements of each subsystem are related to the development and deployment of AI algorithms.
Connected Vehicle

Be Careful: Your Smart Car Could Be Hacked!
We rely on network-connected devices or vehicles every day, but if we ignore the cybersecurity verification of our products, there is a potential risk of significant and potentially life-threatening issues for your consumers.
Cybersecurity has a wide range of definitions.
In automotive industry, T-Box is one of the key points in V2X (Vehicle-to-everything), which is responsible for communicating with the outside world through the Internet of IOV platform. It also a critical protection points for brand owners.
Validation Key Points
-
- Service stability
- Data Security
- Security at the hardware entity level
Any Connected Devices

Prepare Your Validation Before it’s too late!
Cybersecurity will influence all of your RF enabled devices as well. Our goal is to defense the potential cyber threats before it happened.
Allion provide the experienced consultation and customize testing service including Vulnerability Scan or Penetration Testing.
We protect the organization from breaches and the exposure of sensitive data.
Vulnerability scan is the process of identifying security weaknesses and flaws in systems and software running on device. This is an integral component of a vulnerability management program, which has one overarching goal – to protect the organization from breaches and the exposure of sensitive data.
Allion Cybersecurity Validation Coverage

Black Box Detection (Web Vulnerability Scan)
Simulate hacker intrusion attack modes, adopt different attack modes, find vulnerabilities on websites for different purposes, and provide information security reports
White Box Detection (Program Source Code Scan)
The source code inspection provides one positive test and two retests and delivers the documents, and a total of three test result reports are produced.


Penetration Testing
URL penetration test, including a detailed vulnerability description and repair suggestion written report and re-inspection, and remote repair consulting services for each initial/review.
System Vulnerability Scan
Identify vulnerabilities that allow remote attackers to access sensitive information.
Check if the system has the latest software patches.
Try default or common passwords on system accounts, vulnerability analysis, production reports.

*All test reports comply with industry standard normative reports (FISMA, GLBA, HIPAA, SOX, DISA, PCI-DSS, etc.) and regulatory compliance reports (OWASP, WASC, NERC CIPC, ISO 27001, ISO 27002, NIST, CWE/SANS, etc.)