Allion Labs
In the era of the Internet of Things where everything can be connected to the Internet, cyber security has become increasingly important in business operations. As the global epidemic has changed everyone’s daily routines, demands such as video conferencing, home offices, and remote teaching have emerged. The boundary between work and home is becoming less obvious, resulting in home networks becoming targets for hackers.

Home Routers May be Prone to Botnet Viruses
According to news reports in early 2022, more than 10 home routers owned by a well-known manufacturer have been invaded by Russian hackers, spreading botnet viruses. The manufacturer urgently announced countermeasures and rushed to repair the vulnerabilities. However, as of March 2022, most of the infected devices still have not been fixed successfully.
In September 2022, the botnet targeted different brands once again, exploiting loopholes such as CVE-2015-2051, CVE-2018-6530, CVE-2022-26258, and CVE-2022-28958 to invade devices. Most of these devices can be used for RCE attacks, as the CVSS risk score is as high as 9.8 to 10 points, which is very close to a full score.
There are usually two types of situations when a home router is hacked:
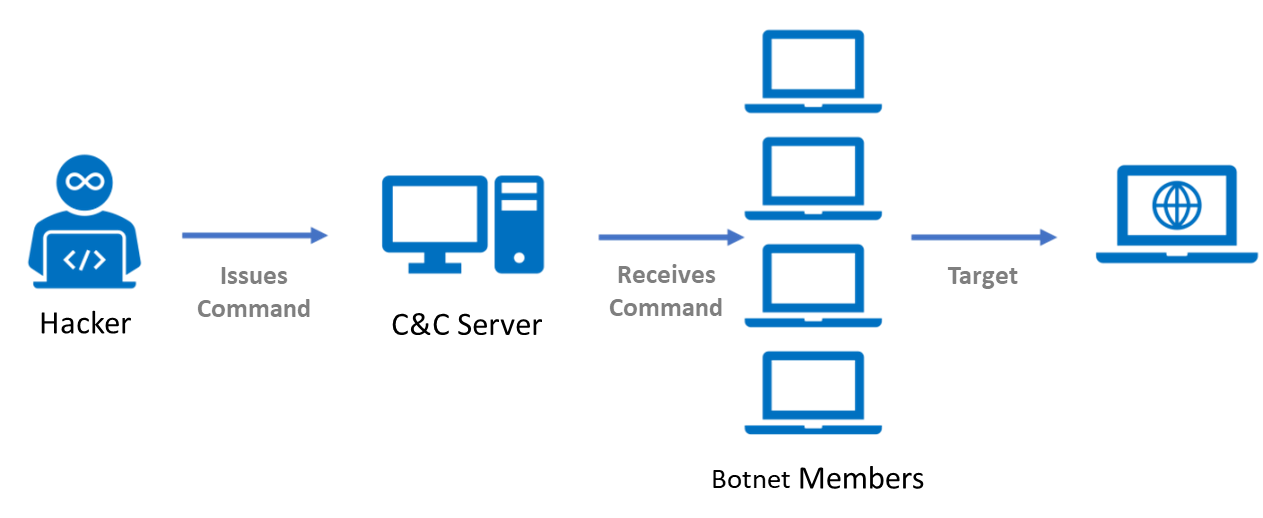
1. Becoming Part of a Botnet
A Botnet refers to the intrusion of computer viruses, hackers, or Trojan horse viruses into devices on a home network, allowing them to control the devices remotely and can quickly launch DDoS attacks, steal personal information, and other malicious behaviors at any time.
2. Getting Used by Hackers for Illegal Mining
Hackers use botnets to remotely control network devices in users’ homes and conduct Bitcoin mining for profit. A well-known antivirus software company in Taiwan once reported in 2018, more than 200,000 routers were hacked for mining. Their approach was to take advantage of the vulnerabilities of the Winbox port (8291) by connecting to it and requesting access to the system user database files.

Why Do Hackers Choose Routers as Targets?
This is because routers must be connected to an outlet for long periods of time and most do not have automatic update mechanisms, so users don’t usually update the routers regularly. Under these circumstances, home routers inherently have more information security vulnerabilities. In addition to the changes in work patterns during the post-pandemic era, the demand for home offices has increased significantly, and opportunities for employees to connect to corporate networks are also growing. With important personal high-value data hidden in home networks, home routers will naturally become obvious prey for hackers.
How to Ensure Router Security
Regarding Internet access at home and home information security, Allion recommends users to pay more attention to the following points:
1. Change Preset Administrator Passwords and Update Passwords Regularly
Usually, there are preset passwords on a new router, but they’re very simple in terms of combination and strength, making it easy to be hacked by malicious programs. If you’re still using the default password, we recommend that you replace it with a stronger password that’s not as easy to guess as early as possible for better security.

2. Set a Wi-Fi Password
If the router doesn’t have a Wi-Fi password, it will quickly become an information security vulnerability that can be easily accessed. In addition, avoid using public Wi-Fi to connect to the Internet as much as possible if you can. This is another good way to effectively reduce the chance of malicious programs hacking your device.
3. Choose a Wi-Fi Protocol With Higher Security
After setting a Wi-Fi password, don’t forget to set the encryption for the wireless network. It’s recommended to use higher security protocols such as WPA2 or WPA3.

4. Regularly Update Your Router
As mentioned before, most users do not know to update routers regularly. Therefore, it’s recommended that you should remember to update the firmware whenever possible to get rid of potential vulnerabilities and prevent malicious programs from entering your network devices at home.
5. Turn Off Specific Functions
Technology evolves from human nature, and risks often come from laziness. Once you greed for convenience, it becomes an opportunity for hackers. Specific functions such as WPS and UPnP are both easy channels for hackers to intrude. A tech website pointed out a few days ago that a total of more than 100,000 routers were hacked from UPnP functions, allowing them to become part of a botnet. Therefore, users are advised to disable certain functions.
6. Monitor Devices Connected to Routers Regularly
When home routers are hacked, other devices connected through the router are very likely to be hacked also. Therefore, users are advised to check whether their routers are connected to an unknown device. Once network speeds slow down and other possibilities are ruled out, it’s very likely that your home router has been hacked.

Allion’s Cybersecurity Lab is Looking Out For You
Whether around the home or in the office, any device that’s connected to the Internet can be hacked. Allion is able to provide fast, effective, and cost-effective information security solutions customized for each product’s characteristics and scenarios that meet international information security standards. Allion can comprehensively investigate potential IoT security vulnerabilities to create a watertight protection system, helping you effectively prevent security risks, potential threats, and even cybercrimes on the Internet.
If you want to know more, we welcome you to visit Allion’s Cybersecurity Lab or contact us through this online form. Allion’s service team will gladly help you!
Technical Highlights