Allion Labs
Have You Ever Used Public Wi-Fi? Be Aware of These Hidden Security Risks
Did you know that these public networks allow for your credit card information, account passwords, and other sensitive information accessible to hackers? Information security experts found that using public Wi-Fi has no privacy at all. It’s the same as directly giving away your personal information to hackers.

In recent years, a Chinese citizen was using public Wi-Fi which resulted in bank deposit theft. Another case that attracted attention was hackers used public Wi-Fi networks of foreign cafés to spread crypto mining programs and illegally used other people’s equipment. Well-known VPN companies also indicated that 25% of tourists use public Wi-Fi when traveling abroad, becoming the victims of hackers. Therefore, information security experts suggest that when you need to use public Wi-Fi outside, you should use a VPN program to encrypt your connection so that third-party programs cannot intercept your valuable data.
Which VPN Should I Use?
There are more uses for VPN programs than people think, such as downloading files or receiving discounts from other countries. Nowadays, more and more people are looking for free VPN programs with easy-to-use interfaces, but the level of security of the program can be the most overlooked part.
Recently, a number of VPN companies have advertised heavily on video platforms. Their main selling points are not recording the connection information and protecting the user’s personal data. Also, through the encrypted connection provided by the VPN program, it can effectively block people who are interested in tracking IP addresses, protecting the user from them. However, VPN programs can only block the possibility of personal data leakage in the process, but they cannot rule out the possibility of being hacked from the source.
First, we can start by understanding how a Virtual Private Network (VPN) works:
- Encryption technology prevents data from being intercepted and used by other parties before it’s transmitted between devices and servers, improving network security.
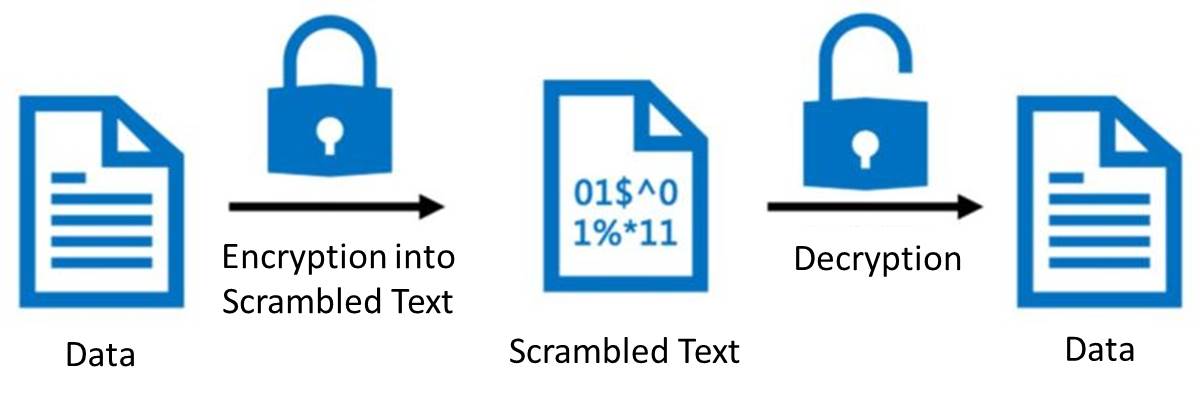
- The virtual connection established by the VPN can also be used for safely accessing important private resources.
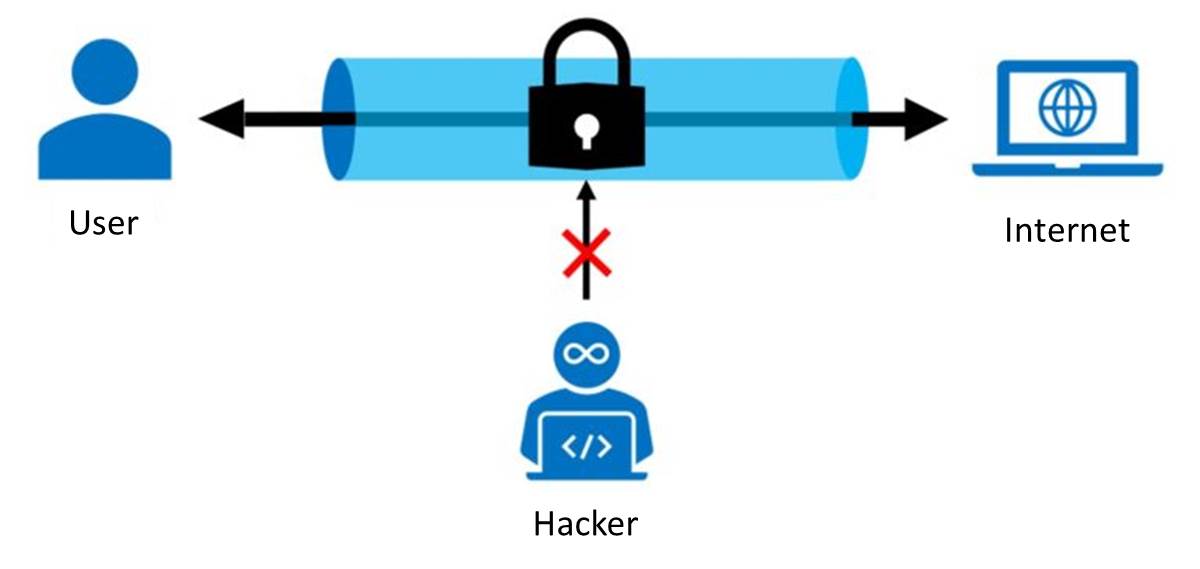
By using the methods above, your IP address browsing history, and online activities won’t be exposed to the world.
Although a VPN has many benefits, they aren’t 100% safe. The main reason for this is that VPN users can only blindly trust the VPN provider’s security system and believe their information will not be leaked. Even with a VPN service, you cannot avoid the risk of being hacked.
How Can I Improve Online Security?
Since the general public doesn’t usually check if their wireless AP needs to be updated after it’s set up or whether passwords are changed regularly, we recommend starting from the source. The following suggestions are provided by Allion professionals for different types of people:
For General Consumers
- When you first receive your device, encrypting the transmission method is a priority
- Avoid using a WEP encryption
- Switch to WPA-PSK/WPA2-PSK for better security
- Use TKIP, AES, TKIP+AES, and other advanced authentication modes
- Change the default AP account password regularly
- Regularly update the firmware to reduce vulnerabilities
For Manufacturers and Brand Owners
- Seek assistance from professional testing laboratories to reduce unnecessary risks
- Use professional third-party security testing tools such as
- Fortify Static Code Analyzer
- CyberRes
- Confirm the following security regulation contents of tests complies with the standards of the European Telecommunications Standards Institute (ETSI)
- Not using a universal default password
- Implementing a method to manage vulnerability reports
- Continuously updating software
- Safe storage of sensitive security parameters
- Communication security
- Minimizing possible cyber attacks
- Ensuring software completion
- Ensuring personal data security
- Checking system
- Making the system resilient to failures
- Checking system remote data
- Allow users to easily delete their data
- Simplify installation and maintenance of their equipment
- Validate input data
(The 13 items above correspond to the contents of the OWASP IoT Top 10)
Following effective information security protocols will ensure the security of your IoT products. Adding AI security testing for software object detection can fully protect user data privacy and effectively maintain your brand’s professionalism.
If you are interested in consultation and assistance from an information security consultant, please fill out this form.