In recent years, cybersecurity threats have continued to escalate as an increasing number of devices such as personal computers and mobile devices become interconnected through cloud services, the Internet of Things (IoT), and cloud-based storage. While data accessibility has improved, it has also given rise to a growing range of security vulnerabilities and malicious attacks. Beyond traditional software-based protection such as antivirus programs, hardware-level security, particularly for storage devices, has become a critical line of defense. One commonly adopted approach is hardware-based encryption, such as AES 256-bit encryption, which performs full disk encryption directly within the storage device through an embedded encryption-capable controller. Compared with software-based encryption, hardware encryption offers significantly higher security, making data extraction from encrypted drives extremely difficult without proper authorization.
As more storage devices are now equipped with encryption capabilities, an important challenge remains. How can users verify that these encryption mechanisms truly meet security standards and are implemented correctly. To address this, the Trusted Computing Group (TCG) established the Opal Storage Specification. Storage products that comply with the TCG Opal specification perform encryption internally at the device level, delivering stronger data protection compared with software-based encryption. As encryption is handled entirely within the device, it does not impact system performance, consume system resources, or require additional encryption components.
To verify compliance with the TCG Opal specification, we collaborate with ULINK Technology, a well-known test tool developer. By utilizing ULINK’s test tools and the TCG’s test scripts, we perform both TCG Opal Certification Tests and TCG Opal Protocol Tests to verify whether products meet the requirements. These TCG-recognized test tools are applied to validate SATA and NVMe storage devices.
Below is an introduction to TCG Opal Certification Test and TCG Opal Protocol Test:
TCG Opal Certification Test
To verify whether the storage device properly meets the TCG specification (TCG Storage Architecture Core Specification, Version 2.01, TCG Storage OPAL Family Test Cases Specification, Version 1.00), certification tests are performed to conduct TCG functional checks on storage devices. These tests validate whether the results fully comply with the specifications.
| a. Use Case Test Cases: | b. Specific Functionality: | c. Error Test Cases: |
| 1. UCT-01 Level 0 Discovery | 1. SPF-01Transaction | 1. ETC-01 Native Protocol Read/Write Locked Error Responses |
| 2. UCT-02 Properties | 2. SPF-02 IF-RECV Behavior Tests | 2. ETC-02 General IF-SEND /IF-RECV Synchronous Protocol |
| 3. UCT-03 Taking ownership of an SID | 3. SPF-03 TryLimit | 3. ETC-03 Invalid IF-SEND Transfer length |
| 4. UCT-04 Activate Locking SP when in Manufactured Inactive State | 4. SPF-04 Tries Reset | 4. ETC-04 Invalid SessionID – Regular Session |
| 5. UCT-05 Configuring Authorities | 5. SPF-05 Tries Reset on Power Cycle | 5. ETC-05 Unexpected Token Outside of Method – Regular Session |
| 6. UCT-06 Configuring Locking Objects (Locking Ranges) | 6. SPF-06 Next | 6. ETC-06 Unexpected Token in Method Header – Regular Session |
| 7. UCT-07 Unlocking Ranges | 7. SPF-07 Host Session Number (HSN) | 7. ETC-07 Unexpected Token Outside of Method – Control Session |
| 8. UCT-08 Erasing Ranges | 8. SPF-08 RevertSP | 8. ETC-08 Unexpected Token in the Method Parameter List – Control Session |
| 9. UCT-09 Using the DataStore table | 9. SPF-09 Range Alignment Verification | 9. ETC-09 Exceeding Transaction Limit |
| 10. UCT-10 Enable MBR Shadowing | 10. SPF-10 Byte Table Access Granularity | 10. ETC-10 Invalid Invoking ID – Get |
| 11. UCT-11 MBR Done | 11. SPF-11 Stack Reset | 11. ETC-11 Invalid Invoking ID – Non-Get |
| 12. UCT-12 Revert the Locking SP using SID, with Locking SP in Mfg state | 12. SPF-12 TPer Reset | 12. ETC-12 Authorization |
| 13. UCT-13 Revert the Admin SP using SID, with Locking SP in Mfg-Inactive state | 13. SPF-13 Authenticate | 13. ETC-13 Malformed ComPacket Header – Regular Session |
| 14. UCT-14 Revert the Admin SP using SID, with Locking SP in Mfg state | 14. SPF-15 Random | 14. ETC-14 Exceed TPer Properties – Regular Session |
| 15. UCT-15 Revert Admin SP using Admin1, with Locking SP in Mfg state | 15. SPF-16 CommonName | 15. ETC-15 Exceed TPer Properties – Control Session |
| 16. UCT-16 Revert Admin SP using PSID, with Locking SP in Manufactured state | 16. SPF-17 DataStore Table | 16. ETC-16 Overlapping Locking Ranges |
| 17. SPF-18 Range Crossing Behavior | 17. ETC-17 Invalid Type | |
| 18. SPF-19 Block SID Authentication | 18. ETC-18 RevertSP – GlobalRange Locked | |
| 19. ETC-19 Activate / ATA Security Interaction | ||
| 20. ETC-20 StartSession on Inactive Locking SP | ||
| 21. ETC-21 StartSession with Incorrect HostChallenge | ||
| 22. ETC-22 Multiple Sessions | ||
| 23. ETC-23 Data RemovalMechanism – Set Unsupported Value |
TCG Opal Protocol Test
Next, to verify whether the Opal Protocol implementation complies with the TCG specifications (TCG Storage Architecture Core Specification, Version 2.01; TCG Storage OPAL Test Cases Specification, Version 1.00), protocol tests are performed to conduct functional checks on the storage device. These tests validate whether the protocol responses fully comply with the specifications.
| a. OPALv1: | b. OPALv2: |
| 1. A0: Identify Device | 1. AlignSet_DataStore |
| 2. A1: Trusted Send/Receive | 2. AlignSet_LBA |
| 3. A2: Protocol ID = 0 related | 3. AlignSet_MBR |
| 4. A3: Level 0 Discovery | 4. Authenticate |
| 5. A4: Synchronous Communication Ptc | 5. Protocol2 |
| 6. A5: ComPacket/Packet/SubPacket | 6. Random |
| 7. A7: Transaction | 7. Revert_Effect2 |
| 8. A8: Ending Session | 8. StackReset |
| 9. A9: Empty Atom | 9. TPerInfo_SSC |
| 10. A10: Properties | 10. TPerReset |
| 11. A11: Start/SyncSession | 11. VerifyGeometry |
| 12. A6: Method_invoke/response | 12. RevertSP_Pyrite1_0 (for Pyrite1.00 device only) |
| 13. A12_Get_Byte_GramChk | 13. DataRemoval |
| 14. A13_Set_Byte_GramChk | 14. StartSyncSession_SessionTO |
| 15. A14_Next_AdminSP_GramChk | c. TableInfo: |
| 16. A15_GetACL_AdminSP_GramChk | 1. C1: Level 0 Discovery contents |
| 17. A19_RevertSP_GramChk | 2. C2: Properties() contents |
| 18. D1_ACESet | 3. C3: Get() contents |
| 19. D2_AuthoritySet | 4. C3_Get_ObjTable_LockSP_All |
| 20. D3_C_PINSet | 5. C4: Next() contents |
| 21. D4_LockingSet_RangeStartLength | 6. C5: GetACL() contents |
| 22. D4_LockingSet_WriteLock | d. Features: |
| 23. D5: MBRControl.Set | 1. Additional_DS |
| 24. D6: MBR.Set | 2. PSID |
| 25. D7: DataStore.Set() | 3. SingleUser |
| 26. D8: K_AES_*.GenKey | 4. BlockSID |
| 27. D9: Activate | |
| 28. D10: Revert()/RevertSP | |
| 29. D10_RevertSP_Effect | |
| 30. D11: Power Cycle |
Here is an example:
TCG-compliant storage devices feature Shadow MBR, which is used for pre-boot authentication. When a user turns on the device, the system first enters this shadow MBR region to perform identity verification. Only after successful authentication does the device proceed to allow normal system access.
In the test item “UCT-10 Enable MBR Shadowing,” the device failed to deliver the expected response in “subcase 2: Set on ACE_MBRControl_Set_DoneToDOR to include User1 and User8; Set Response: Pass“. Therefore, the test result was marked as Fail.
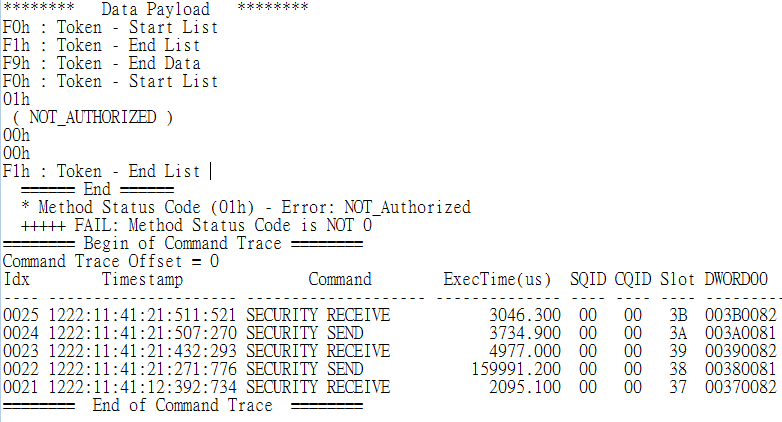
In addition TCG Opal Certification Test and TCG Opal Protocol Test, Allion also offers detailed analysis for tests that fail to meet the requirements, helping manufacturers identify root causes, address issues, and ultimately achieve certification.