Allion Labs
Smart home appliances make people’s lives more convenient, but do you know the hidden risks behind them? According to news reports in 2019, hackers launched attacks on Google streaming devices and smart TVs. Hackers used the Universal Plug and Play (UPnP) protocol to gain control of the set-top box. Through the set-top box, they could then use various devices on the network, so the user’s devices could be operated by the hacker. The confidential information the hacker had access to includes the Wi-Fi network connected to the device, the connection time, paired Bluetooth devices, and even alarm clocks. Although this was not a malicious attack, just a warning from hackers that the products have security problems, it still makes people doubt whether they will be monitored or not.
In 2016, an American citizen named Darren Cauthon encountered a case where his smart TV was infected by a malicious Android program and was blackmailed USD 500 to unlock the device. The situation was resolved by resetting the smart TV.
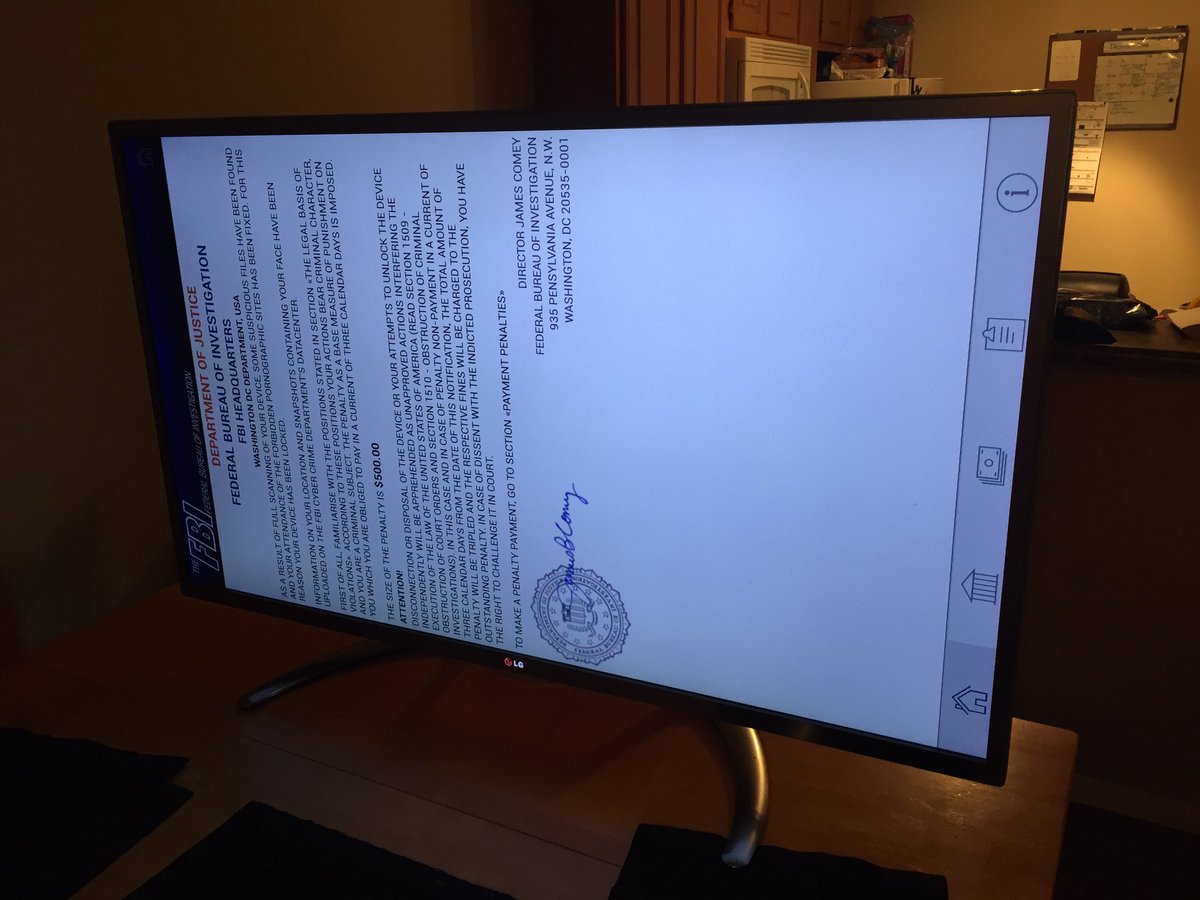
(Source: @darrencauthon)
According to the FBI, compared with mobile phone and laptop manufacturers, TV manufacturers are more likely to ignore the importance of digital security. Due to this reason, the cameras, microphones, or any privacy-related settings of smart TVs may become the hackers’ targets. Not only are set-top boxes riskier, but cable TV systems have also been hacked before. During the Russo-Ukrainian War in 2022, hackers hacked into smart TV systems and issued anti-war slogans.
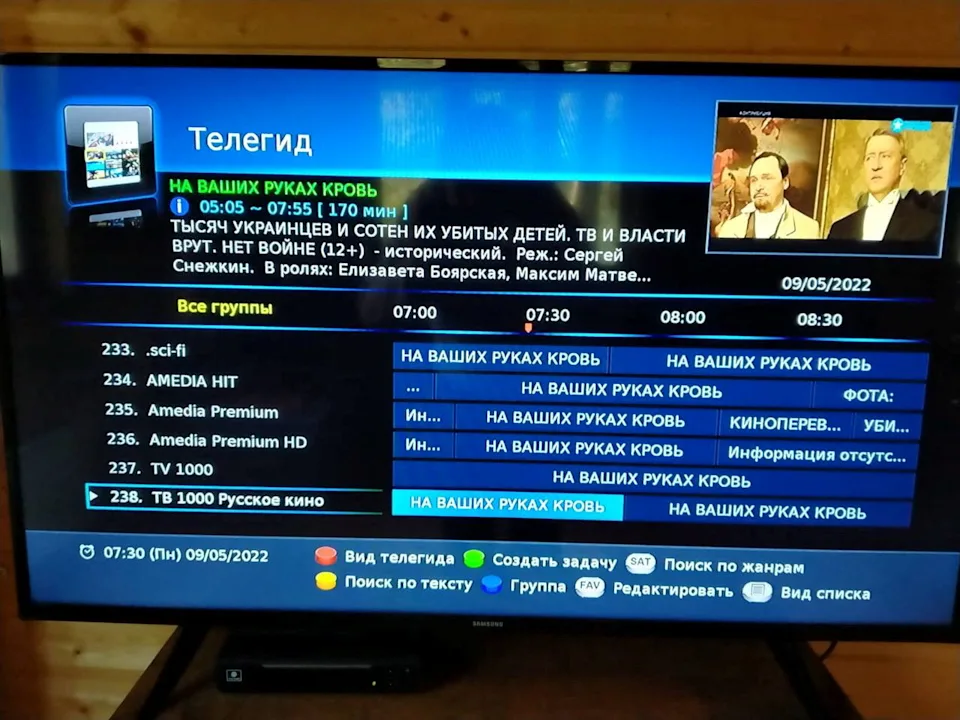
(Source: News)
Privacy and Security Can be Assured With Allion’s Device Testing
Allion has compiled a comprehensive list of issues that people often encounter when using smart devices. We suggest manufacturers conduct security inspections from these three levels:
- Browsing Pirated Audio and Video Websites
- According to statistics from information security industries, the amount of these websites has sharply increased in Taiwan during the COVID-19 level 3 epidemic alert last year. There are many suspicious links hidden in these types of websites. Following the OWASP IoT Top 10 can help you detect IoT vulnerabilities before your product leaves the factory.
- Downloading Unverified Video-on-demand Programs From Unknown Sources
- Hackers like to target people’s greedy mentalities. It’s very easy for hackers to implant malicious programs into free unlimited viewing apps because it’s impossible to track the source. Not only does this violate the law, but it may also leak the user’s credit card information. It’s recommended that information security personnel use third-party tools to detect vulnerabilities and rule out this possibility.
- Purchasing Unverified Set-top Boxes
- As mentioned before, the consequences of being greedy for small gains are often not worth it. Set-top boxes with no brand often cannot be traced back to their manufacturers and whether there are hidden malicious programs inside. In addition, most set-top boxes are based on early Android 4.0 OS. There are common security vulnerabilities in old OS versions and also the problem of not being able to update or patch in time, so it’s necessary to check whether there are any issues with the following list:
- Usability
- System update
- Wi-Fi and Bluetooth testing
- Security report
- Identification
- Engineer mode
- Payment function Identification
- Privacy Encryption
- Login security
- Minimize ports
- Data transmission
- Sensitive data access
- Data record deletion
- Data storage protection
- Security Functions
- Common operating system vulnerabilities
- Physical port security
- Sensitive data storage
- Wi-Fi hotspot
- Built-in software security
- Usability
- As mentioned before, the consequences of being greedy for small gains are often not worth it. Set-top boxes with no brand often cannot be traced back to their manufacturers and whether there are hidden malicious programs inside. In addition, most set-top boxes are based on early Android 4.0 OS. There are common security vulnerabilities in old OS versions and also the problem of not being able to update or patch in time, so it’s necessary to check whether there are any issues with the following list:
After the series of tests mentioned above, we can prevent the majority of consumers’ devices from being infiltrated with malicious programs after installing software or inputting personal information. If you are interested in the risks of smart devices or Allion’s solutions mentioned in this article, feel free to contact us here.